Exploring VTVcab’s router (Dasan H660DW)
This post is a little bit different than usual, having me exploring my ISP router which is the Dasan Networks H660DW, stay with me to see what I’ve found in the process.
Disclaimer: I am not responsible for any damage you cause to your device or ISP by following this guide. Do this at your own risk!
The default IP for this router is 192.168.55.1 or 192.168.56.1, yes it has 2 separated LAN IP address. In this tutorial I’ve changed my Net ID to 192.168.0.0 so the router’s IP will be 192.168.0.1 because it’s faster to type.
The password for this router varies by firmware, it could be admin:vertex25 or admin:SERIAL_NUMBER with SERIAL_NUMBER is the GPON S/N on the label of the router.
1. Specs:
- 1244Mb/s 1310nm DFB Upstream Burst Mode Transmitter
- 2488Mb/s 1490nm APD/TIA Downstream
- 1550nm CATV Receiver
- Triplexer: Hisense LTY9775M
- SC Fiber connector
- 5x1Gbps Ethernet Switch (4 usable)
- 1 CATV RF output
- WIFI: Ralink RT5392L (2.4GHz Wireless access point with 2 Antenna)
- SOC: Ralink MT751020 SOC (4 MIPS core)
- RAM: 128MB
- NAND: 128MB
2. Access SSH/Telnet:
Web interface have a lot of limitation because it’s designed for end user, what you will want to do is to talk with it natively, on some earlier firmware having SSH and Telnet enabled by default but the latest one doesn’t do that, you have to do it manually.
2.1. Enabling SSH/Telnet
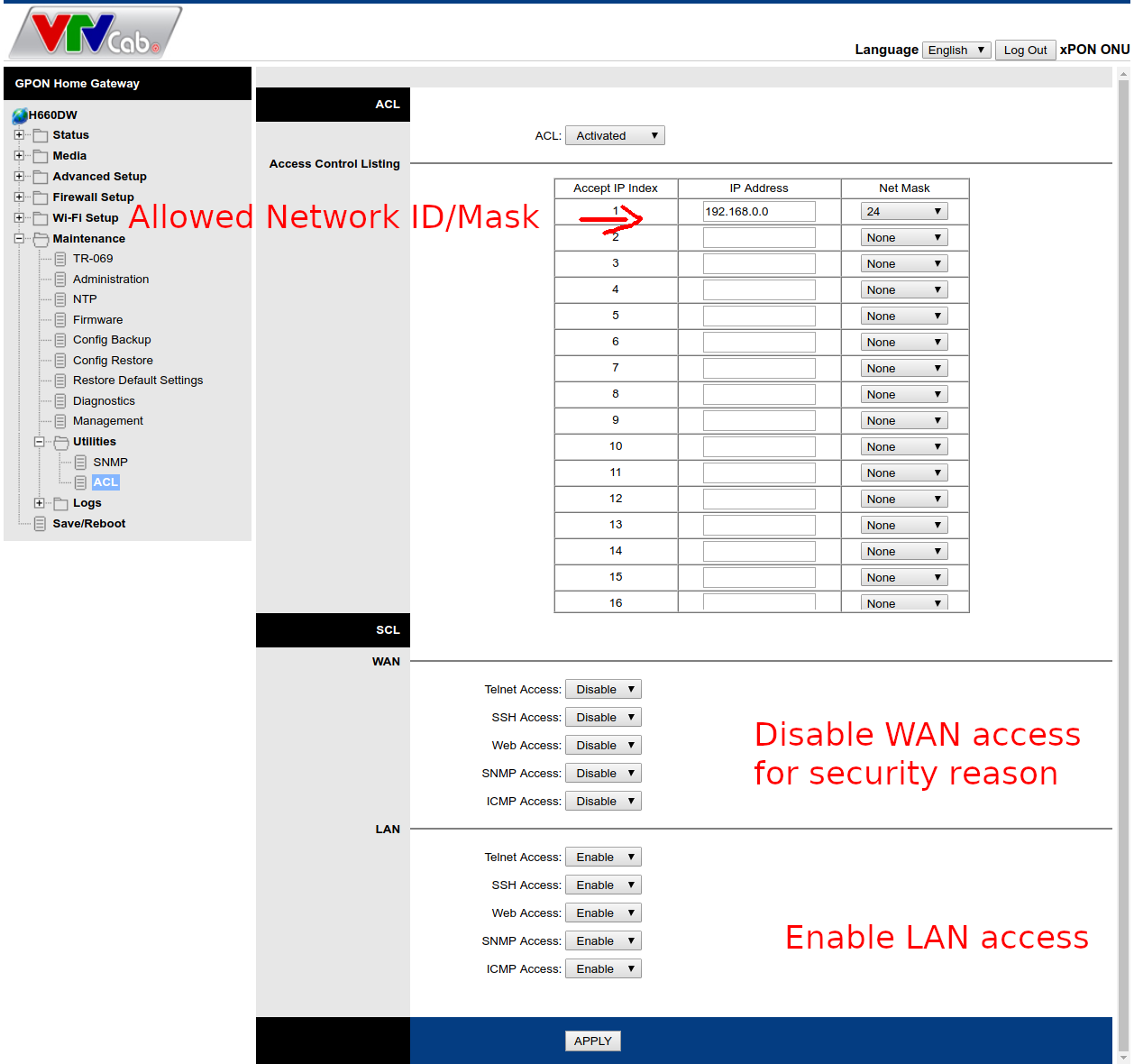
Go to Maintenance -> Utilities -> ACL and set it as the picture below.
ACL: Activated Access Control Listing: This table determines which IP range are allowed to access the router’s features in the SCL.
- IP Address: Put your LAN Network ID here
- Net Mask: This is the range of the Network ID which are allowed to access SCL, 24 means from 192.168.0.0 to 192.168.0.255 SCL: This table is for enable/disable special function access.
- WAN: For security reason, you should disable all the options here so people on the internet couldn’t access your router’s panel.
- LAN: You could enable everything here if you want.
2.2. Accessing SSH:
Now you should be able to access SSH/Telnet using PuTTY on Windows or ssh tools on your favorite Linux distribution.
SSH credential: admin:YOUR_PANEL_PASSWORD
Now there’s something to notice: The router’s SSH server are using a deprecated algorithm for SSH which is not allowed to access by openssh by default, you have to put -oKexAlgorithms=+diffie-hellman-group1-sha1 to the ssh command for login:
[user@Arch-Linux ~]$ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 [email protected]
[email protected]'s password:
# export
export HOME='/'
export LOGNAME='admin'
export PATH='/userfs/bin:/usr/sbin:/bin:/usr/bin:/sbin'
export PWD='/'
export SHELL='/bin/sh'
export TERM='xterm-256color'
export USER='admin'
# pwd
/
# ls
bin data etc linuxrc sbin userfs var
boaroot dev lib proc tmp usr
# uname -a
Linux tc 2.6.36 #1 SMP Thu Jun 22 08:40:46 UTC 2017 mips unknown
#
There we go, we got SSH access, this router is running a MIPS processor with a small Linux on it, the file system is squashfs so you can’t directly modify the file system, it’s not gonna keeping change when you reboot it, the config file is saved on a different partition.
2.3. Accessing Telnet:
This is an exciting one, for some reason, Telnet don’t allow you to login using the control panel’s credentials but it using a different password, I was able to find some documents talking about the password for this.
Telnet credential: admin:vertex25ektks123
[user@Arch-Linux ~]$ telnet 192.168.0.1
Trying 192.168.0.1...
Connected to 192.168.0.1.
Escape character is '^]'.
tc login: admin
Password:
# export
export HOME='/'
export LOGNAME='admin'
export PATH='/userfs/bin:/usr/sbin:/bin:/usr/bin:/sbin'
export PWD='/'
export SHELL='/bin/sh'
export TERM='vt102'
export USER='admin'
#
It’s still the exact same thing as SSH, not that it enable some extra privilege or something and more importantly: You can’t change this password, this is a serious security flaw which allow attacker to logging using a hardcoded credential, I recommeded to disable the telnet function because an attacker could do anything with this telnet access to your router.
3. SSH exploring
Random stuffs I’ve grabbed via SSH goes here:
- Mount point, MTD info:
# mount
/dev/mtdblock3 on / type squashfs (ro,relatime)
proc on /proc type proc (rw,relatime)
ramfs on /tmp type ramfs (rw,relatime)
devpts on /dev/pts type devpts (rw,relatime,mode=600)
/dev/mtdblock8 on /data type jffs2 (rw,relatime)
# ls /dev/mtd*
/dev/mtd /dev/mtd4 /dev/mtdblock0 /dev/mtdblock5
/dev/mtd0 /dev/mtd5 /dev/mtdblock1 /dev/mtdblock6
/dev/mtd1 /dev/mtd6 /dev/mtdblock10 /dev/mtdblock7
/dev/mtd10 /dev/mtd7 /dev/mtdblock2 /dev/mtdblock8
/dev/mtd2 /dev/mtd8 /dev/mtdblock3 /dev/mtdblock9
/dev/mtd3 /dev/mtd9 /dev/mtdblock4
- /proc/cpuinfo:
system type : Ralink MT751020 SOC
processor : 0
cpu model : MIPS 34Kc V5.5
BogoMIPS : 498.07
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes, count: 4, address/irw mask: [0x0000, 0x0ff8, 0x0ff8, 0x0ff8]
ASEs implemented : mips16 dsp mt
shadow register sets : 1
core : 0
VCED exceptions : not available
VCEI exceptions : not available
processor : 1
cpu model : (null) V5.5
BogoMIPS : 374.37
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes, count: 4, address/irw mask: [0x0000, 0x0ff8, 0x0ff8, 0x0ff8]
ASEs implemented : mips16 dsp mt
shadow register sets : 1
core : 0
VCED exceptions : not available
VCEI exceptions : not available
processor : 2
cpu model : (null) V5.5
BogoMIPS : 374.37
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes, count: 4, address/irw mask: [0x0000, 0x0ff8, 0x0ff8, 0x0ff8]
ASEs implemented : mips16 dsp mt
shadow register sets : 1
core : 0
VCED exceptions : not available
VCEI exceptions : not available
processor : 3
cpu model : (null) V5.5
BogoMIPS : 374.37
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes, count: 4, address/irw mask: [0x0000, 0x0ff8, 0x0ff8, 0x0ff8]
ASEs implemented : mips16 dsp mt
shadow register sets : 1
core : 0
VCED exceptions : not available
VCEI exceptions : not available
- /proc/crypto:
name : stdrng
driver : krng
module : kernel
priority : 200
refcnt : 1
selftest : passed
type : rng
seedsize : 0
name : arc4
driver : arc4-generic
module : kernel
priority : 0
refcnt : 1
selftest : passed
type : cipher
blocksize : 1
min keysize : 1
max keysize : 256
name : aes
driver : aes-generic
module : kernel
priority : 100
refcnt : 1
selftest : passed
type : cipher
blocksize : 16
min keysize : 16
max keysize : 32
name : md5
driver : md5-generic
module : kernel
priority : 0
refcnt : 1
selftest : passed
type : shash
blocksize : 64
digestsize : 16
- /proc/mtd: (To calculate actual size of MTD, convert the size column from Hex to Decimal, the result will be the size in Kilobytes)
dev: size erasesize name
mtd0: 00040000 00020000 "bootloader"
mtd1: 00040000 00020000 "romfile"
mtd2: 0013645b 00020000 "kernel"
mtd3: 00770000 00020000 "rootfs"
mtd4: 030e0000 00020000 "tclinux"
mtd5: 001358d7 00020000 "kernel_slave"
mtd6: 00760000 00020000 "rootfs_slave"
mtd7: 02ae0000 00020000 "tclinux_slave"
mtd8: 00200000 00020000 "user_rootfs"
mtd9: 00500000 00020000 "user_config"
mtd10: 000a0000 00020000 "reservearea"
- #ps aux:
PID Uid VmSize Stat Command
1 admin 328 S init
2 admin SW [kthreadd]
3 admin SW [ksoftirqd/0]
4 admin SW [kworker/0:0]
5 admin SW [kworker/u:0]
6 admin SW [migration/0]
7 admin SW [migration/1]
9 admin SW [ksoftirqd/1]
10 admin SW [migration/2]
12 admin SW [ksoftirqd/2]
13 admin SW [migration/3]
14 admin SW [kworker/3:0]
15 admin SW [ksoftirqd/3]
16 admin SW< [khelper]
17 admin SW [sync_supers]
18 admin SW [bdi-default]
19 admin SW< [kblockd]
20 admin SW [kswapd0]
21 admin SW [fsnotify_mark]
22 admin SW< [aio]
23 admin SW< [crypto]
28 admin SW [mtdblock0]
29 admin SW [mtdblock1]
30 admin SW [mtdblock2]
31 admin SW [mtdblock3]
32 admin SW [mtdblock4]
33 admin SW [mtdblock5]
34 admin SW [mtdblock6]
35 admin SW [mtdblock7]
36 admin SW [mtdblock8]
37 admin SW [mtdblock9]
38 admin SW [mtdblock10]
40 admin SW [kworker/3:1]
41 admin SW [kworker/1:1]
42 admin SW [kworker/2:1]
43 admin SW [kworker/0:1]
51 admin SWN [jffs2_gcd_mtd8]
126 admin 2308 S /userfs/bin/cfg_manager
175 admin SW [kworker/u:1]
222 admin SW [pon_phy_task]
336 admin SW [kworker/1:2]
422 admin 60 S tcwdog -t 1 /dev/watchdog
527 admin 56 S /usr/bin/utelnetd -l /bin/login -d
644 admin 2308 S /userfs/bin/cfg_manager
645 admin 2308 S /userfs/bin/cfg_manager
646 admin 2308 S /userfs/bin/cfg_manager
647 admin 2308 S /userfs/bin/cfg_manager
648 admin 2308 S /userfs/bin/cfg_manager
650 admin 596 S /userfs/bin/epon_oam
652 admin 1276 S /userfs/bin/omci
1480 admin 308 S /userfs/bin/dropbear
1606 admin 324 S /usr/sbin/udhcpd
1941 admin 44 S /usr/bin/manager_watchdog
3130 admin 308 S /sbin/syslogd -l 5 -m 0 -O /data/log/messages -o /data/log/sec_messages -S -s 512
3134 admin 296 S /sbin/klogd
3370 admin 736 S /userfs/bin/boa -c /boaroot -d
3489 admin 452 S /bin/sh /usr/script/telnet_checker.sh
3516 admin 452 S /bin/sh /usr/script/cpu_usage_check.sh
3530 admin 2308 S /userfs/bin/cfg_manager
3531 admin 2308 S /userfs/bin/cfg_manager
3532 admin 596 S /userfs/bin/epon_oam
3535 admin 596 S /userfs/bin/epon_oam
3555 admin 596 S /userfs/bin/epon_oam
3558 admin 596 S /userfs/bin/epon_oam
3606 admin 596 S /userfs/bin/epon_oam
3651 admin 300 S /userfs/bin/nos_upgrade
3652 admin 300 S /userfs/bin/nos_upgrade
3654 admin 300 S /userfs/bin/nos_upgrade
3879 admin SW [kworker/2:2]
3997 admin 92 S init
4002 admin 1276 S /userfs/bin/omci
4003 admin 1276 S /userfs/bin/omci
4004 admin 1276 S /userfs/bin/omci
4005 admin 1276 S /userfs/bin/omci
4006 admin 1276 S /userfs/bin/omci
4007 admin 1276 S /userfs/bin/omci
4008 admin 1276 S /userfs/bin/omci
4009 admin 1276 S /userfs/bin/omci
4010 admin 1276 S /userfs/bin/omci
9092 admin 552 S pppd unit 0 user vtv_XXXXXXX password XXXXXX nodetach holdoff 4 maxfail 0 usepeerdns lcp-echo-interval 60 lcp-echo-failure 3 plugin libpppoe.so nas0 defaultroute noipdefault persist mtu
11069 admin 100 S /sbin/udhcpc -i nas6 -s /usr/script/udhcpc_nodef.sh -p /var/run/udhcpc-nas6.pid -m XX:XX:XX:XX:XX:XX
12286 admin 1620 S /userfs/bin/snmpd -Ln -c /etc/snmp/snmpd.conf -p /var/log/snmpd.pid
14266 admin 304 S /userfs/bin/dnsmasq
22612 admin 552 S /userfs/bin/dropbear
22906 admin 500 S -sh
27644 admin 92 S sleep 5
27727 admin 92 S sleep 10
27756 admin 340 R ps aux
- #ls /boaroot/cgi-bin (notice these files, there will be more fun after this)
OutVariant.asp adv_nat_alg_switch.asp cfm_mip.asp home_wireless_5g.asp reboot.asp tools_update.asp
WLAN_Scheduling.asp adv_nat_dmz.asp cfm_status.asp home_wireless_cht.asp ssid_index2.asp upnp_portforward_list.asp
access_URLfilter.asp adv_nat_ipaddrmap.asp cfm_status_log.cgi home_wizard.asp status.asp video_status.asp
access_acl.asp adv_nat_porttriggering.asp current_users.asp index.asp status_deviceinfo.asp virsvr_table.cgi
access_acl2.asp adv_nat_porttriggering_list.asp gem_rate.cgi index_new.asp status_deviceinfo_bhati.asp wifiqa_advanced.asp
access_appfilter.asp adv_nat_top.asp gem_rate_info.asp index_org.asp status_dhcp.asp wifiqa_advanced_cht.asp
access_auth.asp adv_nat_virsvr.asp getCANames.cgi ipaddr_table.cgi status_log.cgi wifiqa_apstatistics.asp
access_auth_registerID.asp adv_ontmode.asp getCertNames.cgi loginFail.asp status_log_bhati.cgi wifiqa_basic.asp
access_cwmp.asp adv_portbinding.asp help_access.asp logout.cgi status_new.asp wifiqa_wmm.asp
access_ddns.asp adv_pvidsetting.asp help_advanced.asp more_client_list.asp status_statistics.asp wizardBridge.asp
access_ipfilter.asp adv_qos.asp help_index.asp more_client_list_2.asp tools_admin.asp wizardConType.asp
access_l2filter.asp adv_qoslist.asp help_interface.asp more_client_list_3.asp tools_admin_cht.asp wizardDHCP.asp
access_l3filter.asp adv_routepolicy.asp help_maintenance.asp navigation-access.asp tools_autoprovision.asp wizardPPP.asp
access_l4appctrl.asp adv_routepolicy_summary.asp help_quickstart.asp navigation-advanced.asp tools_config_backup.asp wizardStatic.asp
access_parental.asp adv_routepolicy_url_summary.asp help_status.asp navigation-basic.asp tools_config_restore.asp wizardTZ.asp
access_snmp.asp adv_routing.asp home_advancedwireless.asp navigation-help.asp tools_factory_restore.asp wizardclose.asp
access_sshd.asp adv_routing_table.asp home_lan.asp navigation-left-cht.asp tools_firmware.asp wizardcomp.asp
access_upnp.asp adv_static_route.asp home_pvclist.asp navigation-left.asp tools_management.asp wizardpwd.asp
admin.asp adv_vlan_group.asp home_servlist.asp navigation-maintenance.asp tools_remove_tftp.cgi wizardset.asp
adv_6rdtunnel.asp adv_vlan_pvid.asp home_setup.asp navigation-status.asp tools_save.asp wizardstart.asp
adv_adsl.asp adv_vlan_top.asp home_wan.asp navigation-status_ssid2.asp tools_system.asp
adv_firewall.asp adv_vpn_connection.asp home_wan2.asp navigation.asp tools_test.asp
adv_fonnet.asp adv_vpn_setting.asp home_wan2_setup.asp portbinding_table.asp tools_tftp.asp
adv_gpon.asp cfm_action.asp home_wan2_setup_cht.asp porttriggering_list.cgi tools_tftp.cgi
adv_ipv6_static_route.asp cfm_mep.asp home_wireless.asp pppoe_pwd.cgi tools_time.asp
- Unencrypted config file is located at /tmp/var/romfile.cfg
3. Web interface vulnerables:
This router have a security issue which allows anyone to access its .cgi page without any password.
As you can see above, we have some .cgi pages
cfm_status_log.cgi getCANames.cgi ipaddr_table.cgi porttriggering_list.cgi status_log.cgi tools_remove_tftp.cgi virsvr_table.cgi
gem_rate.cgi getCertNames.cgi logout.cgi pppoe_pwd.cgi status_log_bhati.cgi tools_tftp.cgi
Most of them is not that interesting but take a look at these files:
- pppoe_pwd.cgi: This file will show the password of the PPPoE account running inside the router, it only show PPPoE Password but not Username though…
- status_log.cgi: This file will reading from /data/log/messages which is the device’s syslogd, there’s nothing much interesting in it, it could also can access via Maintenance -> Logs -> System Log in the web interface.
- status_log_bhati.cgi: This is the most interesting one, it’s the kernel kmsg which having the router’s MAC Address in there, the GPON S/N is a MAC Address and also very similar to the one you could get in here, assuming the router is exposed on the internet, anyone could access this file and try to login using this MAC address (assuming the user didn’t changed the default password and this router’s default password is the GPON S/N)
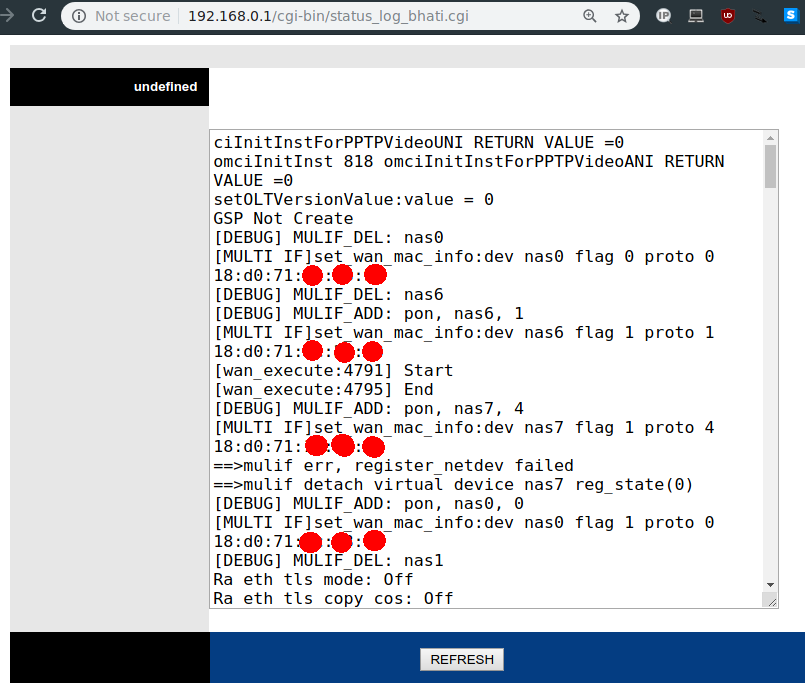
Update: Actually not needed to knowing the Router’s MAC address, just use the hardcoded Telnet password and you’ll get in easily.
Also the Web Interface password is not hashed, it is encoded using base64 and saved in the romfile.cfg, you could even get the data from the export command to print out environment variables in Telnet (SSH don’t have these)
# export
export DS_CONFIG_CONSOLE_PASSWD='dmVydGV4MjVla3RrczEyMw=='
export DS_CONFIG_CONSOLE_USERNAME='admin'
...
export DS_CONFIG_WEB_ACC_NAME_0='admin'
export DS_CONFIG_WEB_ACC_NAME_1='user'
export DS_CONFIG_WEB_ACC_NAME_2='guest'
export DS_CONFIG_WEB_ACC_NUM='3'
export DS_CONFIG_WEB_ACC_PASSWD_0='dmVydGV4MjU='
export DS_CONFIG_WEB_ACC_PASSWD_1='MTIzNA=='
export DS_CONFIG_WEB_ACC_PASSWD_2='MTIzNA=='
4. Firmware hacking
The device having a populated UART header and an unpopulated JTAG header on the board, this is what get spilled out at the UART when boot
DRAMC V2.0 (0)
DRAMC V2.0.0.1 (0)
MT751020 at Wed Dec 16 00:42:14 KST 2015 version 1.6.0 free bootbase
Memory size 128MB
NAND Page size:2048B,Total size 128MB
bmt pool size: 81
Press 's' key in 3 secs to enter boot command mode.
............................................................
Invalid Power GPIO, just return and don't turn on Power LED
==> boot flag = 0
Decompress to 80002000 free_mem_ptr=80600000 free_mem_ptr_end=80780000
from main
Uncompressing [LZMA] ... done.
busybox init and set aff
init started: BusyBox v1.00 (2017.06.22-08:43+0000) multi-call binary
chmod: /userfs/profile.cfg: Read-only file system
Unlocking bootloader ...
Writing from /tmp/boot.bin to bootloader ...
[ w ]
TCSUPPORT_IPV6
net.netfilter.nf_conntrack_max = 8196
net.netfilter.nf_conntrack_tcp_timeout_established = 3600
net.netfilter.nf_conntrack_tcp_timeout_close = 10
net.netfilter.nf_conntrack_tcp_timeout_close_wait = 10
net.netfilter.nf_conntrack_tcp_timeout_time_wait = 10
net.netfilter.nf_conntrack_tcp_timeout_last_ack = 10
chmod: /etc/xml/xml: Read-only file system
mtd[readflash]:device=reservearea tclen=512 tcoffset=524288
Unlocking reservearea ...
Reading from reservearea to /tmp/RT30xxEEPROM.bin ...
mtd[readflash]:device=reservearea tclen=64 tcoffset=525312
Unlocking reservearea ...
Reading from reservearea to /tmp/wlan_cal_info ...
Error--MCL activate value is NULL.
modprobe: could not parse modules.dep
The kernel doesn't support the ebtables 'filter' table.
modprobe: could not parse modules.dep
The kernel doesn't support the ebtables 'filter' table.
modprobe: could not parse modules.dep
The kernel doesn't support the ebtables 'filter' table.
Cannot find device "br0"
insmod raeth driver
cat: /proc/tc3162/hwnat_wan_account: No such file or directory
route: SIOC[ADD|DEL]RT: No such device
==>wlan_read:ioctl open fail
TCSUPPORT_WLAN
iptables: No chain/target/match by that name.
TCSUPPORT_WLAN_MULTIDRIVER
SIOCGIFFLAGS: No such device
done
TCSUPPORT_WLAN: ifconfig
SIOCSIFADDR: No such device
SIOCGIFFLAGS: No such device
interface rai0 does not exist!
telnetd: starting
port: 23; login program: /bin/login
SSH
four ports
SIOCGIFFLAGS: No such device
interface eth0.1 does not exist!
sh: vconfig: not found
SIOCGIFFLAGS: No such device
interface eth0.2 does not exist!
sh: vconfig: not found
SIOCGIFFLAGS: No such device
interface eth0.3 does not exist!
sh: vconfig: not found
SIOCGIFFLAGS: No such device
interface eth0.4 does not exist!
sh: vconfig: not found
device eth0 is already a member of a bridge; can't enslave it to bridge br0.
Added VLAN with VID == 1 to IF -:eth0:-
WARNING: VLAN 1 does not work with many switches,
consider another number if you have problems.
Added VLAN with VID == 2 to IF -:eth0:-
Added VLAN with VID == 3 to IF -:eth0:-
Added VLAN with VID == 4 to IF -:eth0:-
mtd[readflash]:device=reservearea tclen=1 tcoffset=541696
Unlocking reservearea ...
Reading from reservearea to /tmp/bootflag ...
mtd[readflash]:device=tclinux tclen=32 tcoffset=16
Unlocking tclinux ...
Reading from tclinux to /tmp/main_trx.bin ...
mtd[readflash]:device=tclinux tclen=4 tcoffset=0
Unlocking tclinux ...
Reading from tclinux to /tmp/main_magic.bin ...
mtd[readflash]:device=tclinux_slave tclen=32 tcoffset=16
Unlocking tclinux_slave ...
Reading from tclinux_slave to /tmp/slave_trx.bin ...
mtd[readflash]:device=tclinux_slave tclen=4 tcoffset=0
Unlocking tclinux_slave ...
Reading from tclinux_slave to /tmp/slave_magic.bin ...
mtd[readflash]:device=reservearea tclen=1 tcoffset=541696
Unlocking reservearea ...
Reading from reservearea to /tmp/boot_flag_read ...
00:00:17 imgr.c [71]: Initial system driver.
00:00:17 imgr.c [77]: Initial pthread parameters.
00:00:17 imgr.c [83]: Initial dispatcher.
00:00:17 dspch_init.c [23]: Create IPC trap message queue
00:00:17 dspch_init.c [36]: Create IPC trap message queue
00:00:17 imgr.c [89]: Initial database manager.
00:00:17 dbmgr_init.c [32]: Create database memory.
00:00:17 dbmgr_init.c [38]: Create the share database memory successful.
00:00:17 dbmgr_init.c [41]: The total share database size is 0.
00:00:17 imgr.c [95]: Initial config manager.
00:00:17 imgr.c [101]: Initial fault manager.
00:00:17 imgr.c [107]: Initial performance manager.
insmod: cannot insert `/lib/modules/2.6.36/kernel/net/ipv4/netfilter/iptable_filter.ko': File exists (-1): File exists
chmod: /userfs/profile.cfg: Read-only file system
/etc/isp0.conf
/usr/script/wan_start_boot.sh: 925: Syntax error: end of file unexpected
/etc/isp1.conf
/etc/isp2.conf
Cannot find device "imq0"
bad action parsing
parse_action: bad value (5:mirred)!
Illegal fw "action"
/etc/isp3.conf
/etc/isp4.conf
/etc/isp5.conf
/etc/isp6.conf
/etc/isp7.conf
conntrack v1.2.2 (conntrack-tools): connection tracking table has been emptied.
method = HW_NAT_TAB_CLEAN
done
iptables: No chain/target/match by that name.
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
RTNETLINK answers: No such file or directory
conntrack v1.2.2 (conntrack-tools): connection tracking table has been emptied.
method = HW_NAT_TAB_CLEAN
done
SIOCDIFADDR: Cannot assign requested address
SIOCDIFADDR: Cannot assign requested address
killall: dropbear: no process killed
udhcpd (v0.9.9-pre) started
Jan 1 00:00:23 udhcpd[1606]: udhcpd (v0.9.9-pre) started
Unable to open /etc/udhcpd.leases for reading
Jan 1 00:00:23 udhcpd[1606]: Unable to open /etc/udhcpd.leases for reading
sh: /userfs/bin/dproxy: not found
killall: wscd: no process killed
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
chmod: /userfs/profile.cfg: Read-only file system
iptables: Chain already exists.
sh: cannot create /proc/tc3162/qos_switch: Directory nonexistent
/etc/lanAlias0.conf
killall: klogd: no process killed
killall: syslogd: no process killed
ftp switch turn on
sip switch turn on
h323 switch turn on
rtsp switch turn on
l2tp switch turn on,sw_state=
iptables: Bad rule (does a matching rule exist in that chain?).
ipsec switch turn on,sw_state=
iptables: Bad rule (does a matching rule exist in that chain?).
pptp switch turn on
done
killall: boa: no process killed
killall: telnet_checker.sh: no process killed
killall: tftpd: no process killed
killall: inetd: no process killed
send: Broken pipe
mkdir: Cannot create directory `/tmp/cwmp': File exists
mtd[writeflash]:device=reservearea tclen=1 tcoffset=541696 tcfilelen =2
Unlocking reservearea ...
Writing from /tmp/boot_flag_write to reservearea ...
enter real action -----tclen:0x1,tcoffset:0x84400
writeflash: write 0 'st sector,start from 0x80000,0x1 bytes
[e] [w] writeflash: total write 0x1 bytes
cp: /etc/udhcp_lease: No such file or directory
cp: /etc/udhcp_external_lease: No such file or directory
sendEponOamCmdMsg open message queue fail!
Unlocking romfile ...
Writing from /tmp/var/romfile.cfg to romfile ...
[ ] [e] [w] [w] [w] [w] [w]
rai0 no private ioctls.
rai0 no private ioctls.
rai0 no private ioctls.
switch qos type: sp.
switch qos base : 2. (port-based:0, tag-based:1, dscp-based:2, acl-based:3, arl-based:4, stag-based:5)
write reg: 44, value: 227222
dir: 0, port: 6, rate: 1000000
write reg: 1640
write val: 7a12808f
net.ipv4.conf.all.arp_filter = 1
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
^MT7530 switch kernel API (002D, 0, 00000000) return -1 !
^MT7530 switch kernel API (002D, 1, 00000000) return -1 !
iptables: Chain already exists.
^MT7530 switch kernel API (002D, 2, 00000000) return -1 !
^MT7530 switch kernel API (002D, 3, 00000000) return -1 !
device ra1 is not a slave of br0
device ra2 is not a slave of br0
device ra3 is not a slave of br0
unregister_netdevice: waiting for ra0 to become free. Usage count = 1
device ra0 is already a member of a bridge; can't enslave it to bridge br0.
device ra1 is not a slave of br0
device ra2 is not a slave of br0
device ra3 is not a slave of br0
killall: wscd: no process killed
Interface doesn't accept private ioctl...
set (8BE2): Invalid argument
killall: rtdot1xd: no process killed
Ralink DOT1X daemon, version = '2.5.0.0'
Please press Enter to activate this console.
This console is the same as the Telnet console, nothing special about it.
The unencrypted ROM configuration file is located at /tmp/var/romfile.cfg, it is a clear text XML file which contains all the configuration data (Panel password, PPPoE account, WiFi…) and it get written to /dev/mtd1 when you save configuration and get loaded on boot.
To write the romfile.cfg to the romfile partition, use this command:
/userfs/bin/mtd write /tmp/var/romfile.cfg romfile